Reference #
- 基于 ISE 对 Cisco 网络设备部署 AAA
- Configure ASR9K TACACS with Cisco Identity Services Engine 2.4
- Cisco IOS XR Task ID Reference Guide, Release 4.1
本文章是自己配置 ISE 过程的总结,主要参考的是上面文章, 其中最主要的是第一篇(知乎),我认为是最全的 ISE 配置介绍。
ISE Setup(3.1) #
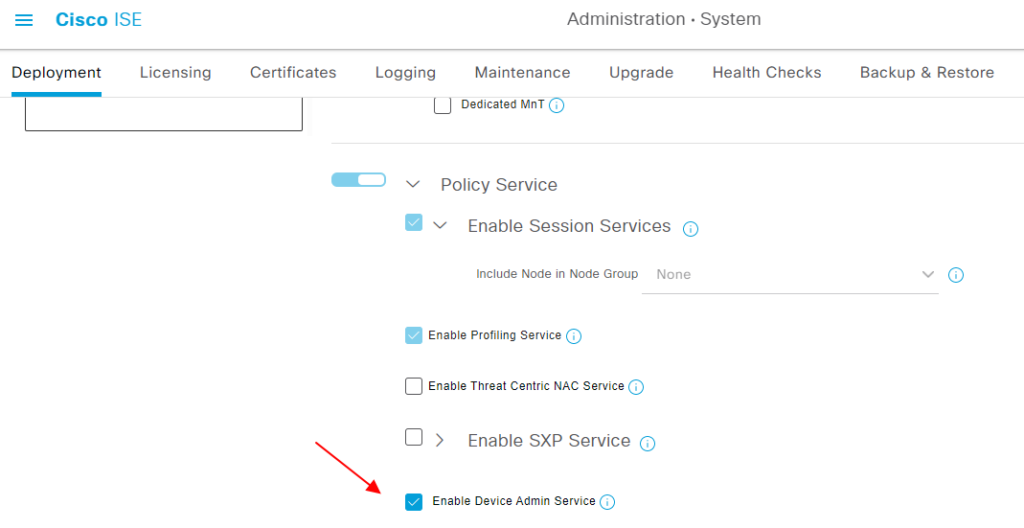
ISE 启用设备管理 #
Administration->System->Deployment
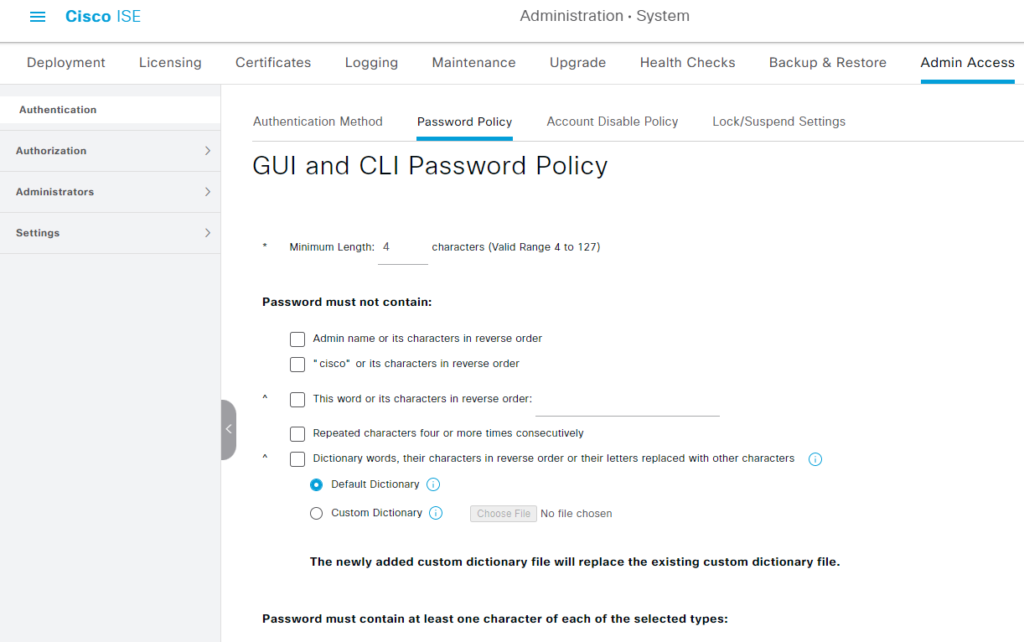
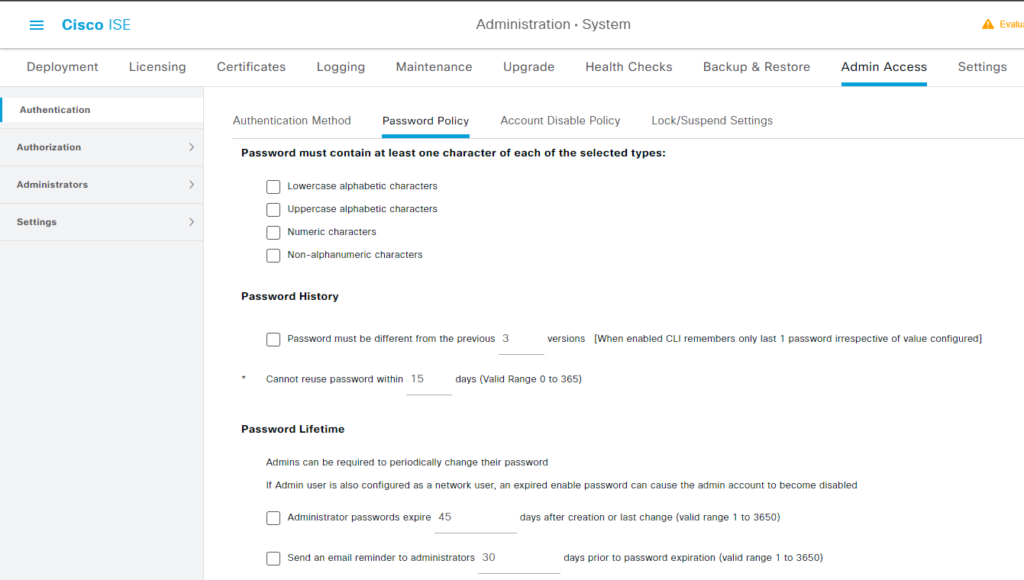
关闭系统密码策略 #
Administration->System->Admin Access->Authentication->Password Policy
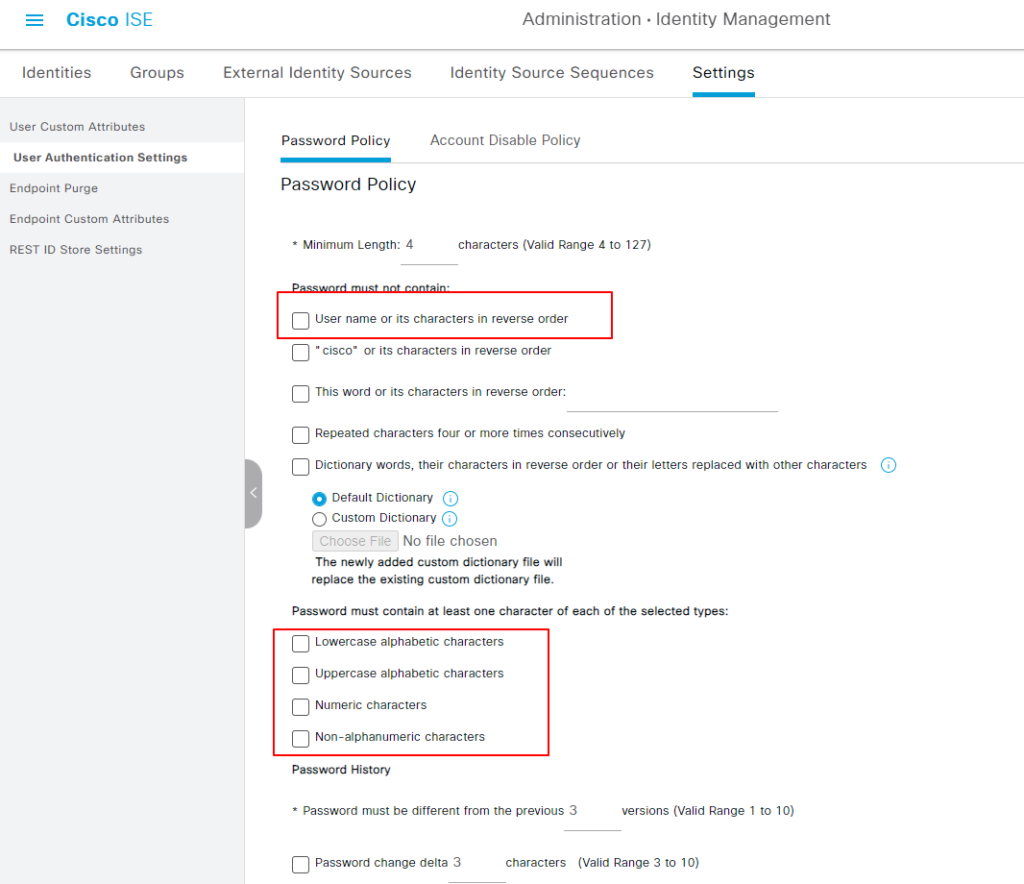
取消所有的选项。
关闭网络设备用户认证的密码策略 #
Administration-> Identity Management -> Settings ->User Authentication Settings ->Password Policy
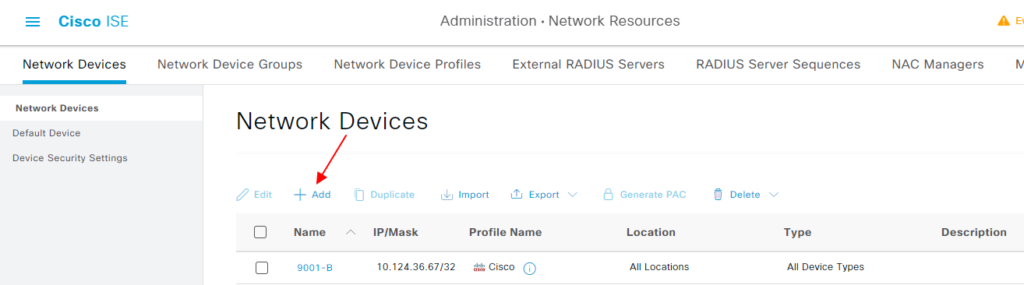
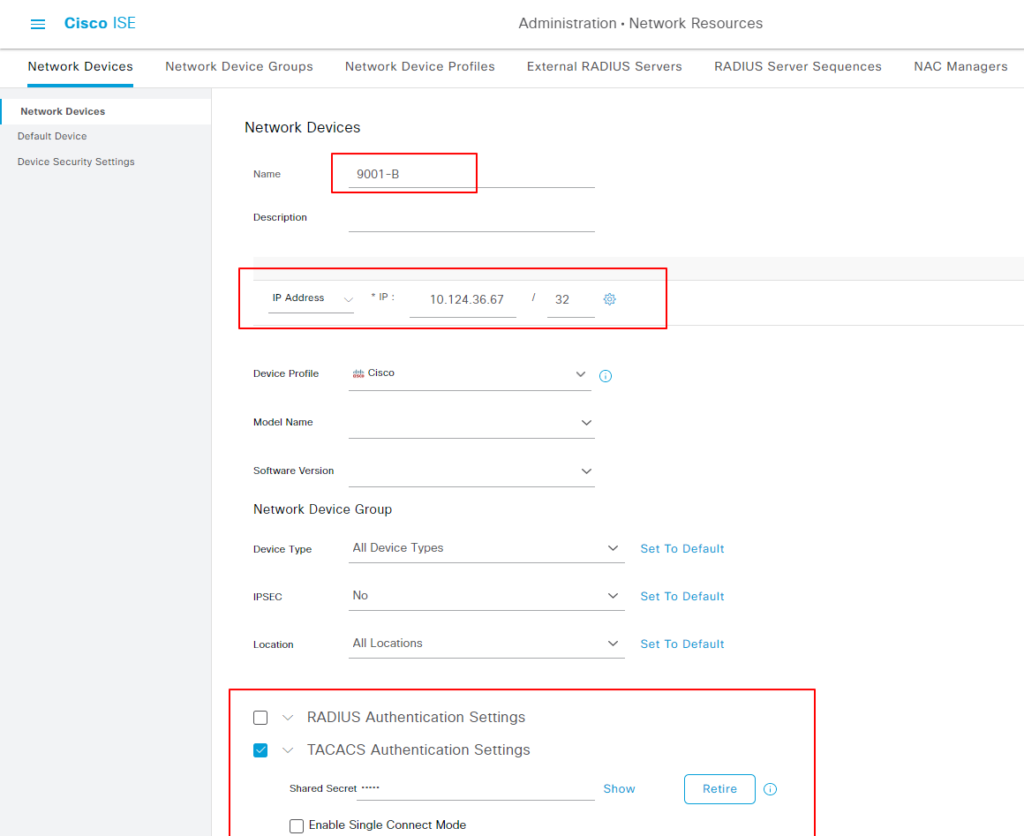
添加网络设备 #
Administration-> Network Resources -> Network Devices
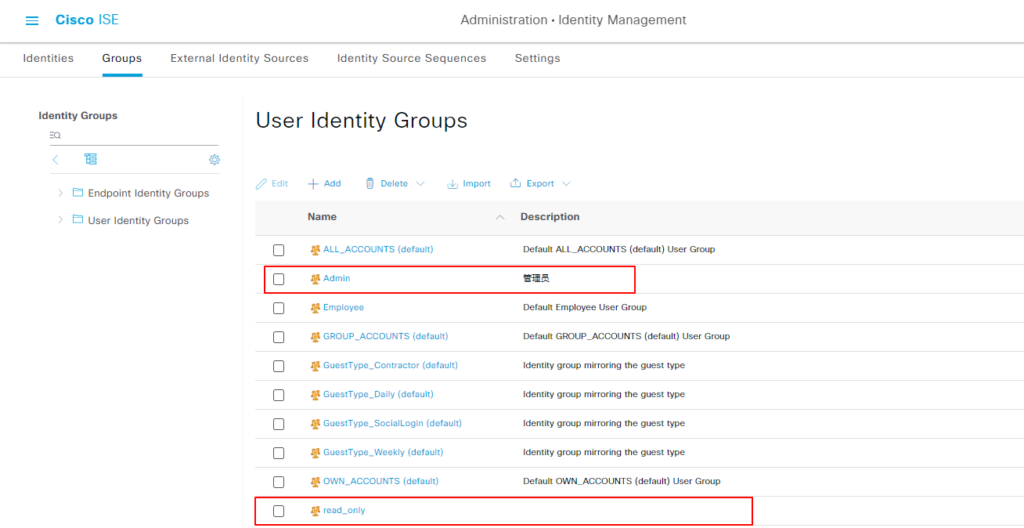
创建用户组/用户 #
Administration->Identity Management ->User Identity Groups
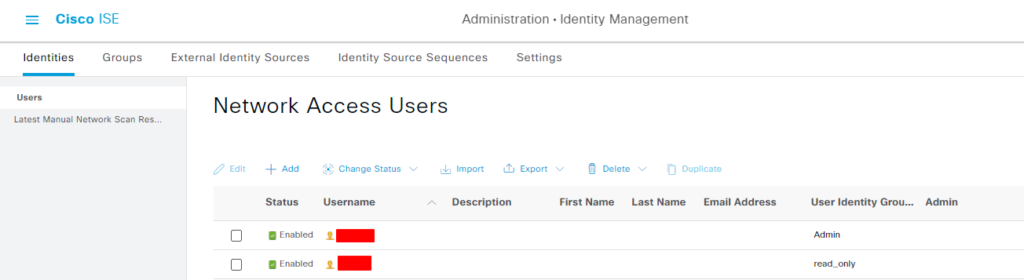
新创建两个组,Admin 和 read_only.
Administration->Identity Management ->Identities
创建两个用户, 并加入之前创建的两个组中.
TACACS 认证授权 #
认证 #
Work Centers -> Device Administration ->Device Admin Policy Sets -> Policy Sets
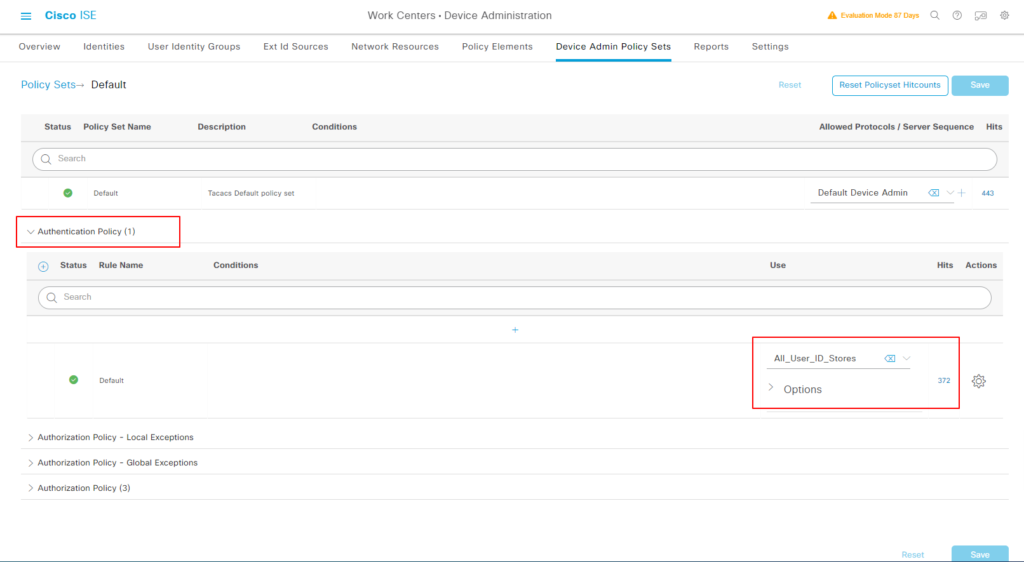
认证保持默认的 default 策略, All_User_ID_Stores
授权 #
我们需要先去创建几个授权策略, 路径: Work Centers -> Device Administration ->Policy Elements -> Results - >Tacacs Command Sets /Tacacs Profiles
Tacacs Profiles #
Profiles 来定义用户属于哪个权限组,比如如下创建两个 profile, tacacs_1 和 tacacs_2
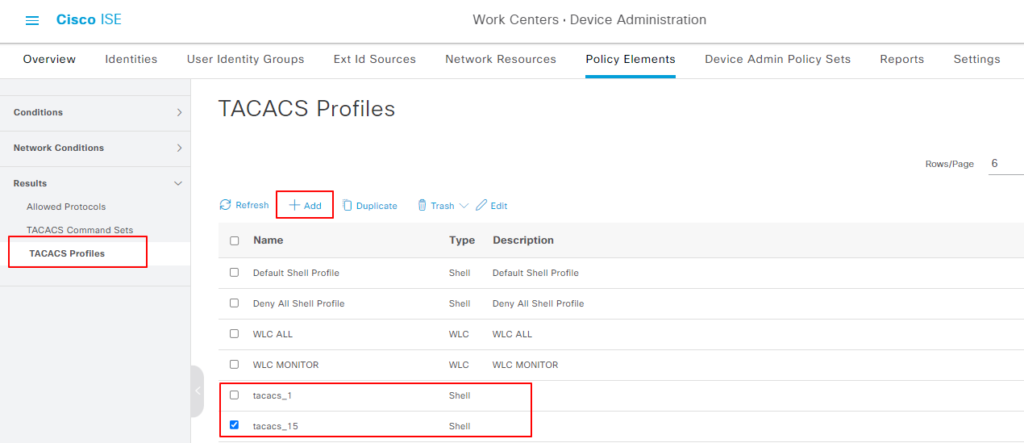
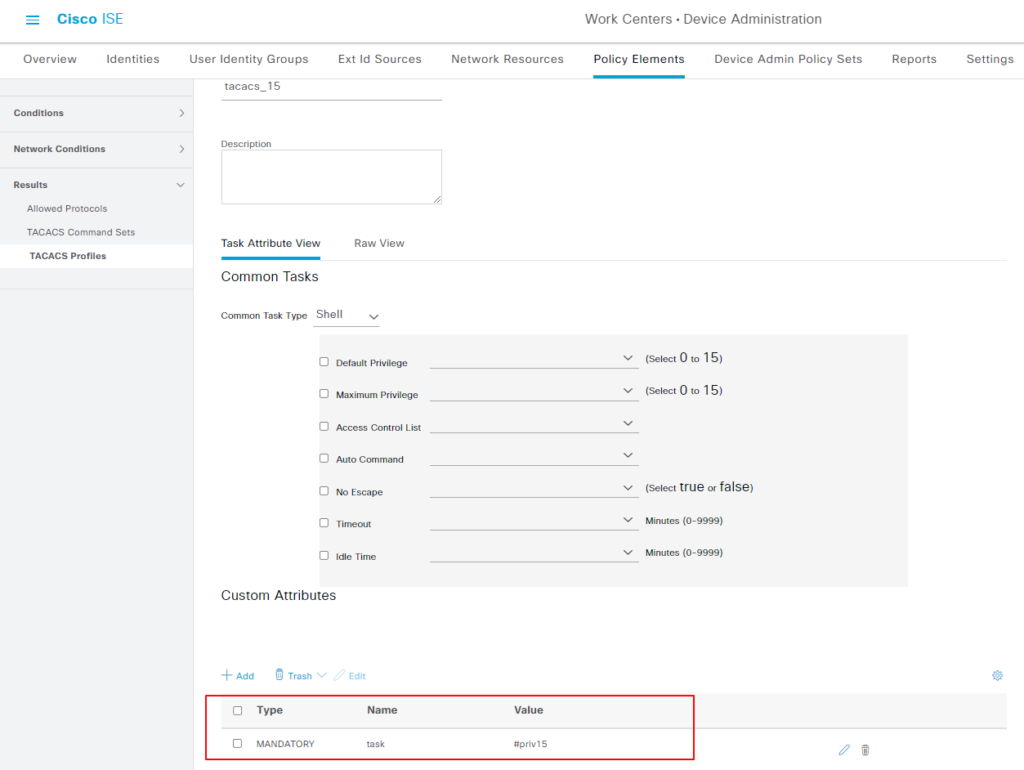
以 tacacs_15 为例,Value 字段为“#priv15”, #号后面代表的 usergroup name, 是 IOS XR 设备上客户自定义的 usergroup name.
参考配置案例。
当然你可以使用设备本身存在的一些 usergroup, 如#sysadmin, #root-system 等
RP/0/RSP0/CPU0:ASR9001-B#show aaa usergroup ?
| Output Modifiers
priv1 Name of the usergroup
priv2 Name of the usergroup
priv5 Name of the usergroup
priv6 Name of the usergroup
priv10 Name of the usergroup
priv15 Name of the usergroup
root-lr Name of the usergroup
netadmin Name of the usergroup
operator Name of the usergroup
sysadmin Name of the usergroup
ugtestct Name of the usergroup
retrieval Name of the usergroup
maintenance Name of the usergroup
root-system Name of the usergroup
provisioning Name of the usergroup
read-only-tg Name of the usergroup
serviceadmin Name of the usergroup
cisco-support Name of the usergroup
WORD Name of the usergroup
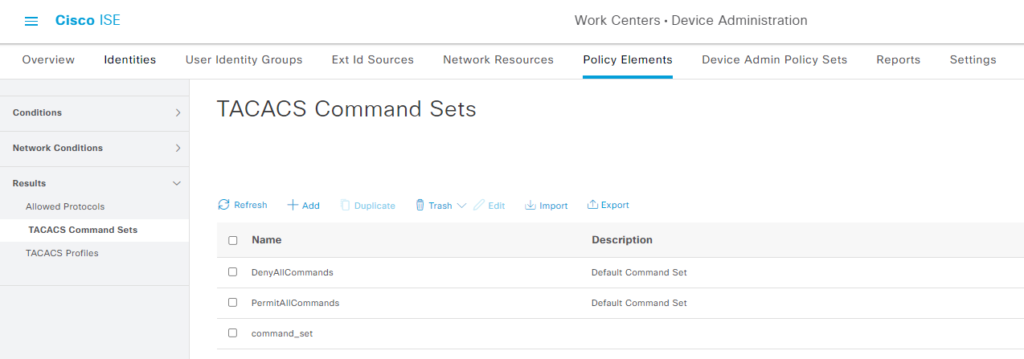
Tacacs Command Sets #
Command Sets 是在 profile 的基础上再次定义哪些命令你可执行,或不可执行。
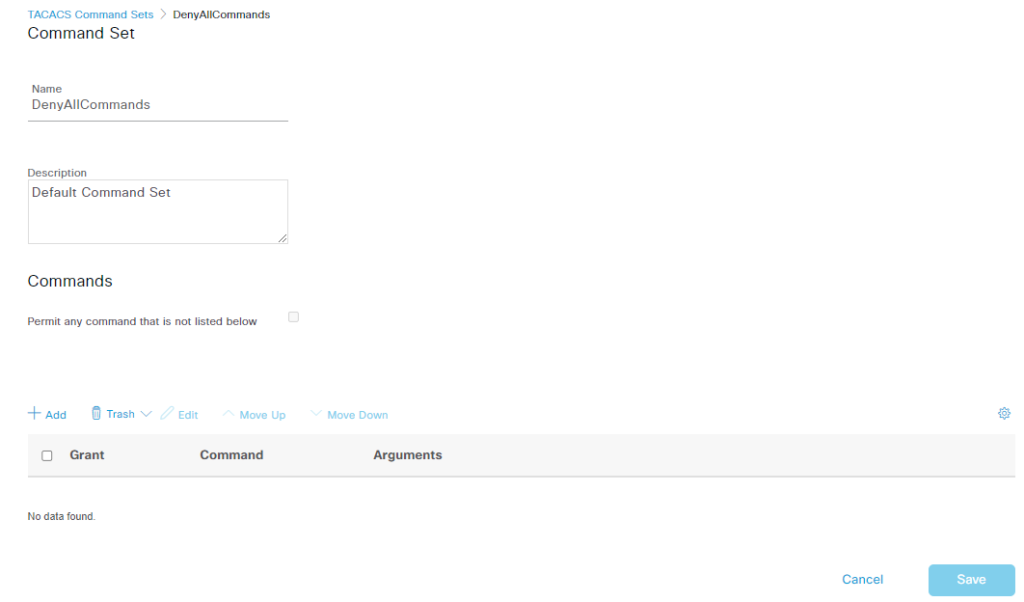
如下我们配置几个 command sets 测试, deny all/permit all/others
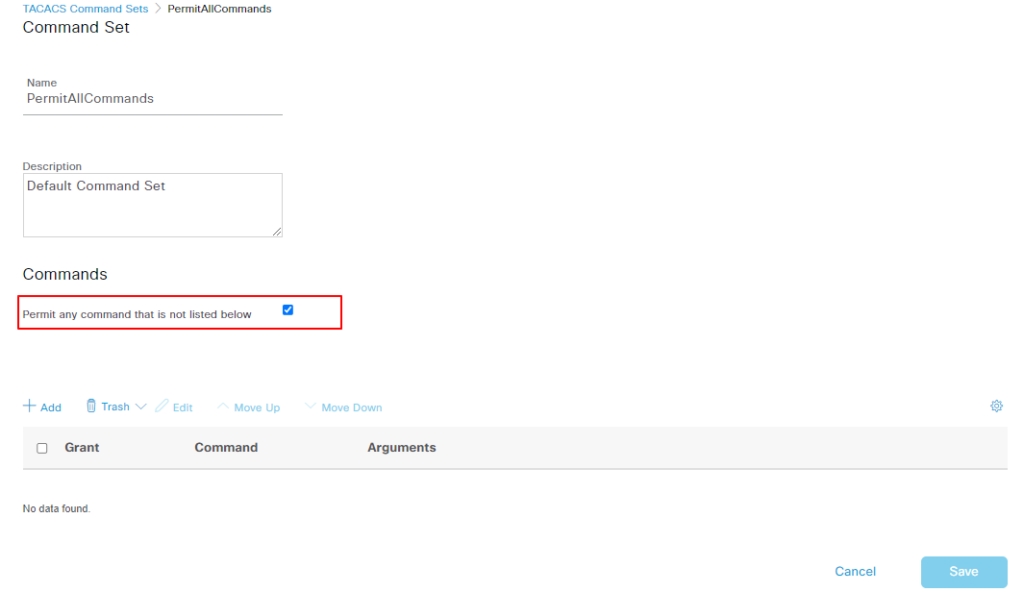
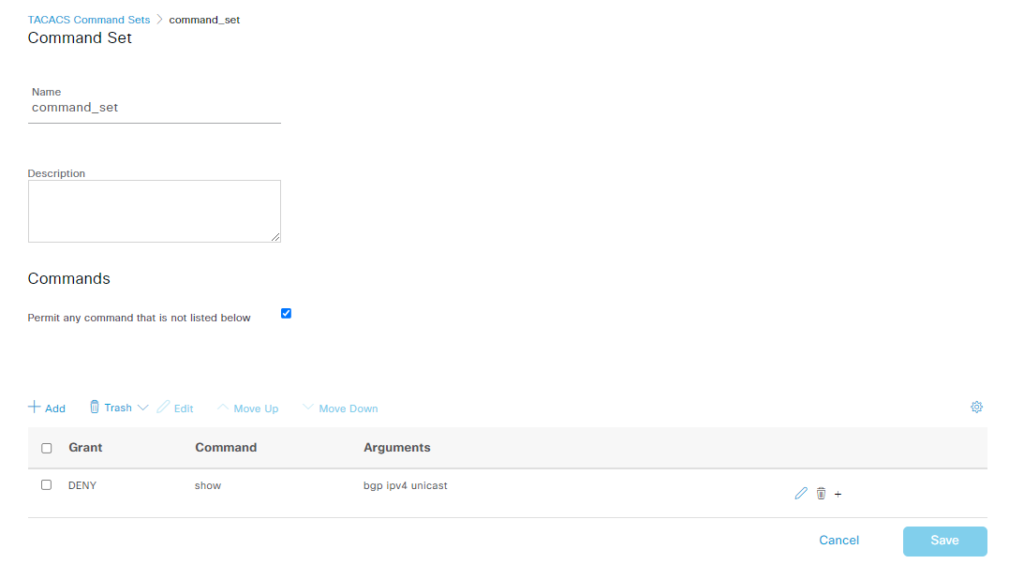
Arguments 可以使用正则表达式
授权关联 Profile #
Work Centers -> Device Administration ->Device Admin Policy Sets -> Policy Sets
[
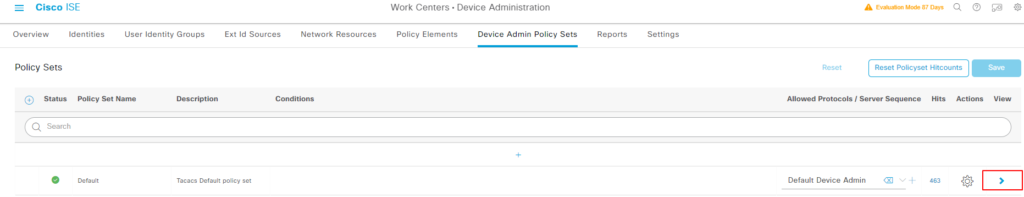
“Insert New Row above”, 创建两个 policy.
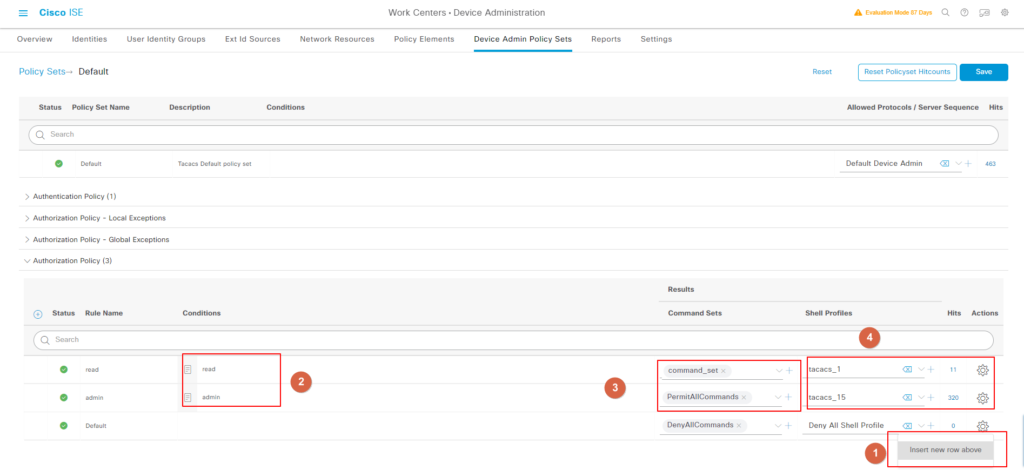
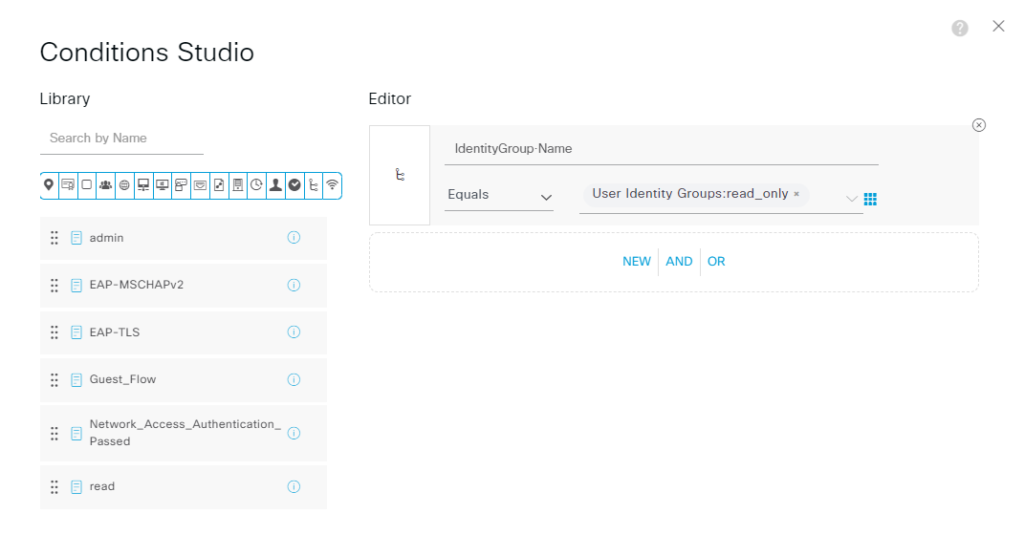
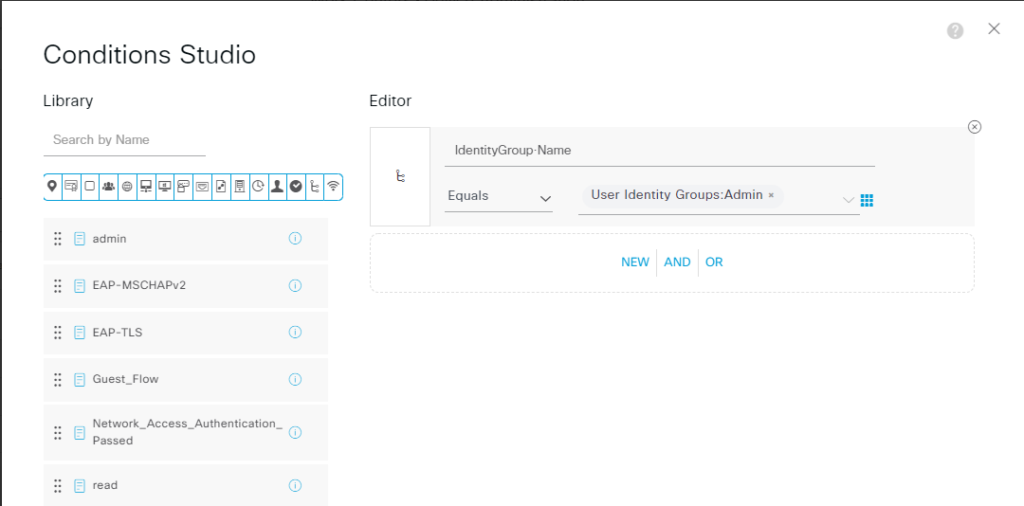
“Conditions"我们用之前创建的用户组来区分,比如用户组属于 read_only 和 Admin, 我们可以分别设置 profile 和 command set.
验证: #
#priv1, “show bgp ipv4 unicast” 这个命令被 command_set deny 掉了。
RP/0/RSP0/CPU0:ASR9001-B#show user group
Mon Feb 21 04:11:30.571 UTC
priv1
RP/0/RSP0/CPU0:ASR9001-B#show user tasks
Mon Feb 21 04:11:35.231 UTC
Task: basic-services : READ WRITE EXECUTE
Task: bgp : READ
Task: interface : READ
Task: ipv4 : READ
Task: isis : READ
RP/0/RSP0/CPU0:ASR9001-B#
RP/0/RSP0/CPU0:ASR9001-B#show bgp ipv4 unicast
Command authorization failed
% Incomplete command.
RP/0/RSP0/CPU0:ASR9001-B#show bgp summary
Mon Feb 21 04:29:56.690 UTC
BGP router identifier 11.1.1.1, local AS number 64072
BGP generic scan interval 60 secs
Non-stop routing is enabled
BGP table state: Active
Table ID: 0xe0000000 RD version: 4
BGP main routing table version 4
BGP NSR Initial initsync version 4294967295 (Not Reached)
BGP NSR/ISSU Sync-Group versions 0/0
BGP scan interval 60 secs
BGP is operating in STANDALONE mode.
Process RcvTblVer bRIB/RIB LabelVer ImportVer SendTblVer StandbyVer
Speaker 4 1 4 0 1 0
Neighbor Spk AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down St/PfxRcd
100.1.12.1 0 18084 0 0 0 0 0 00:00:00 Idle
172.16.10.161 0 18084 0 0 0 0 0 00:00:00 Idle
RP/0/RSP0/CPU0:ASR9001-B#
#priv15
RP/0/RSP0/CPU0:ASR9001-B#show user group
Mon Feb 21 04:29:08.725 UTC
priv15
RP/0/RSP0/CPU0:ASR9001-B#show us
usb user users
RP/0/RSP0/CPU0:ASR9001-B#show user
user users
RP/0/RSP0/CPU0:ASR9001-B#show user tasks
Mon Feb 21 04:29:14.366 UTC
Task: aaa : READ WRITE EXECUTE DEBUG
Task: acl : READ WRITE EXECUTE DEBUG
Task: admin : READ WRITE EXECUTE DEBUG
<snip>
Task: vpdn : READ WRITE EXECUTE DEBUG
Task: vrrp : READ WRITE EXECUTE DEBUG
RP/0/RSP0/CPU0:ASR9001-B#