GRE 简介 #
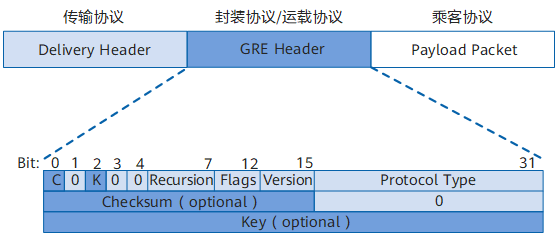
通用路由封装协议 GRE(Generic Routing Encapsulation)可以对某些网络层协议(如 IPX、ATM、IPv6、AppleTalk 等)的数据报文进行封装(区别于 IPsec, IPsec 只能封装 IP 数据包),使这些被封装的数据报文能够在另一个网络层协议(如 IPv4)中传输。
GRE 封装格式 #
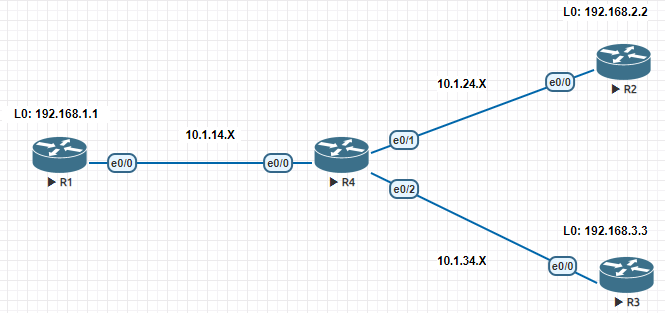
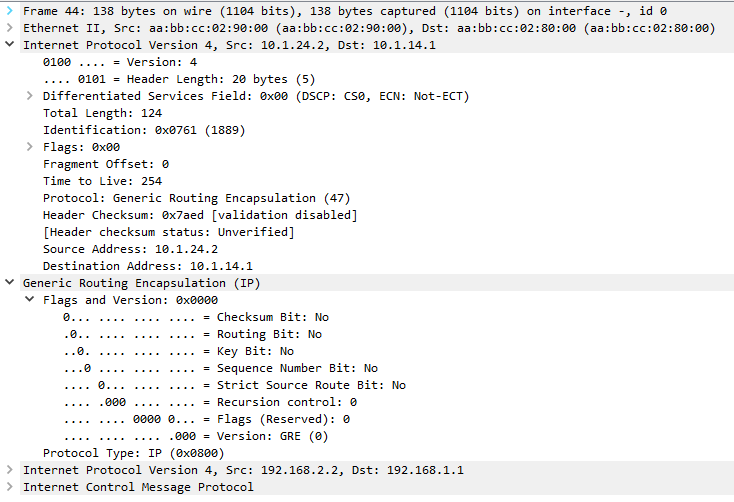
GRE Tunnel 配置 #
interface Tunnel12
ip address 172.16.12.1 255.255.255.0
tunnel source Ethernet0/0
tunnel destination 10.1.24.2
IPSEC over GRE 配置 #
Step 1:IKE Phase 1 #
R1(config)#crypto isakmp policy 1
R1(config-isakmp)# encr aes
R1(config-isakmp)# hash md5
R1(config-isakmp)# authentication pre-share
R1(config-isakmp)# group 2
R1(config-isakmp)# lifetime 30000
R1(config-isakmp)#?
ISAKMP commands:
authentication Set authentication method for protection suite
default Set a command to its defaults
encryption Set encryption algorithm for protection suite
exit Exit from ISAKMP protection suite configuration mode
group Set the Diffie-Hellman group
hash Set hash algorithm for protection suite
lifetime Set lifetime for ISAKMP security association
no Negate a command or set its defaults
Step 2: IKE Phase 2 #
R1(config)#crypto ipsec transform-set TS ah-sha-hmac esp-3des
R1(cfg-crypto-trans)# mode tunnel
R1(config)#crypto ipsec transform-set TS ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
ah-sha256-hmac AH-HMAC-SHA256 transform
ah-sha384-hmac AH-HMAC-SHA384 transform
ah-sha512-hmac AH-HMAC-SHA512 transform
comp-lzs IP Compression using the LZS compression algorithm
esp-3des ESP transform using 3DES(EDE) cipher (168 bits)
esp-aes ESP transform using AES cipher
esp-des ESP transform using DES cipher (56 bits)
esp-gcm ESP transform using GCM cipher
esp-gmac ESP transform using GMAC cipher
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-null ESP transform w/o cipher
esp-seal ESP transform using SEAL cipher (160 bits)
esp-sha-hmac ESP transform using HMAC-SHA auth
esp-sha256-hmac ESP transform using HMAC-SHA256 auth
esp-sha384-hmac ESP transform using HMAC-SHA384 auth
esp-sha512-hmac ESP transform using HMAC-SHA512 auth
Step 3: 配置 Pre-share Key #
R1(config)#crypto isakmp key 6 ccie address 10.1.24.2
R1(config)#crypto isakmp key 6 ccie address 10.1.34.3
Step 4: 配置 IPSec Profile,并在 Tunnel 接口调用 #
R1(config)#crypto ipsec profile PF
R1(ipsec-profile)# set transform-set TS
R1(ipsec-profile)#int tu12
R1(config-if)#tunnel protection ipsec profile PF
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
10.1.14.1 10.1.34.3 QM_IDLE 1001 ACTIVE
10.1.24.2 10.1.14.1 QM_IDLE 1006 ACTIVE
10.1.34.3 10.1.14.1 QM_IDLE 1002 ACTIVE
IPv6 Crypto ISAKMP SA
R1#show crypto ipsec sa
interface: Tunnel13
Crypto map tag: Tunnel13-head-0, local addr 10.1.14.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.14.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (10.1.34.3/255.255.255.255/47/0)
current_peer 10.1.34.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 1188, #pkts encrypt: 1188, #pkts digest: 1188
#pkts decaps: 1189, #pkts decrypt: 1189, #pkts verify: 1189
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.1.14.1, remote crypto endpt.: 10.1.34.3
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x4940E097(1228988567)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xFE32E1FF(4264747519)
transform: esp-3des ,
in use settings ={Tunnel, }
conn id: 13, flow_id: SW:13, sibling_flags 80004070, crypto map: Tunnel13-head-0
sa timing: remaining key lifetime (k/sec): (4177267/1704)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
spi: 0x56983F1B(1452818203)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 13, flow_id: SW:13, sibling_flags 80004070, crypto map: Tunnel13-head-0
sa timing: remaining key lifetime (k/sec): (4177267/1704)
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound pcp sas:
outbound esp sas:
spi: 0x7AB384DD(2058585309)
transform: esp-3des ,
in use settings ={Tunnel, }
conn id: 14, flow_id: SW:14, sibling_flags 80004070, crypto map: Tunnel13-head-0
sa timing: remaining key lifetime (k/sec): (4177267/1704)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
spi: 0x4940E097(1228988567)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 14, flow_id: SW:14, sibling_flags 80004070, crypto map: Tunnel13-head-0
sa timing: remaining key lifetime (k/sec): (4177267/1704)
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound pcp sas:
interface: Tunnel12
Crypto map tag: Tunnel12-head-0, local addr 10.1.14.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.1.14.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (10.1.24.2/255.255.255.255/47/0)
current_peer 10.1.24.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 201, #pkts encrypt: 201, #pkts digest: 201
#pkts decaps: 200, #pkts decrypt: 200, #pkts verify: 200
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.1.14.1, remote crypto endpt.: 10.1.24.2
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x44BBFF5A(1153171290)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x1659CBA9(374983593)
transform: esp-3des ,
in use settings ={Tunnel, }
conn id: 17, flow_id: SW:17, sibling_flags 80000070, crypto map: Tunnel12-head-0
sa timing: remaining key lifetime (k/sec): (4301490/2700)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
spi: 0xC614FC02(3323264002)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 17, flow_id: SW:17, sibling_flags 80000070, crypto map: Tunnel12-head-0
sa timing: remaining key lifetime (k/sec): (4301490/2700)
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound pcp sas:
outbound esp sas:
spi: 0xEB07616B(3943129451)
transform: esp-3des ,
in use settings ={Tunnel, }
conn id: 18, flow_id: SW:18, sibling_flags 80000070, crypto map: Tunnel12-head-0
sa timing: remaining key lifetime (k/sec): (4301490/2700)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
spi: 0x44BBFF5A(1153171290)
transform: ah-sha-hmac ,
in use settings ={Tunnel, }
conn id: 18, flow_id: SW:18, sibling_flags 80000070, crypto map: Tunnel12-head-0
sa timing: remaining key lifetime (k/sec): (4301490/2700)
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound pcp sas:

R1#ping 192.168.2.2 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/6 ms