测试环境介绍 #
使用 SDWAN Deployment Tool 启动一个 20.12.5 的环境,增加两个 cEdge; Tool 会自动配置 DIA 以及基本的 Template, 所以后续只需要增加 ZBFW 的 Policy 即可。
vManage 配置步骤 #
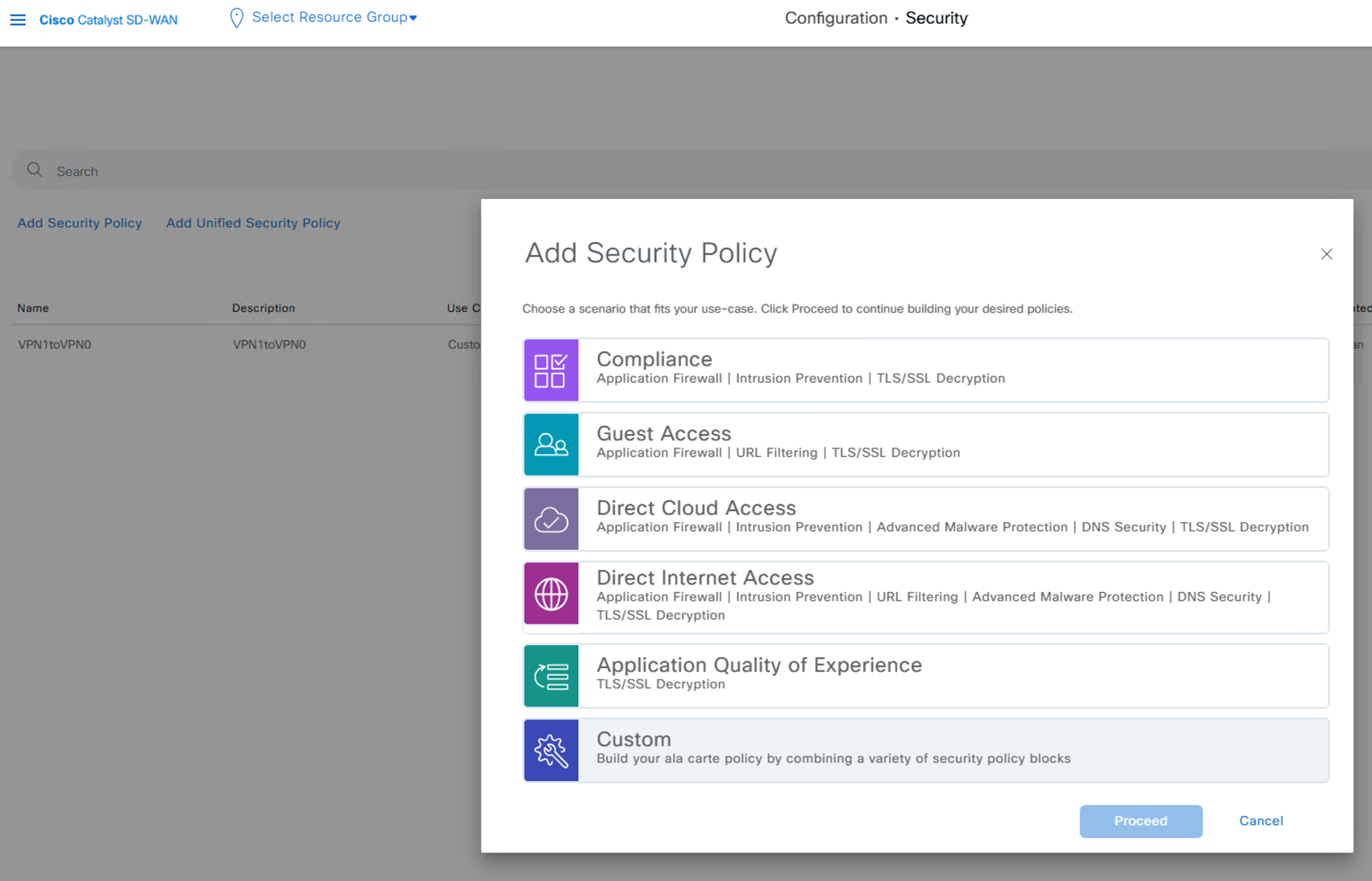
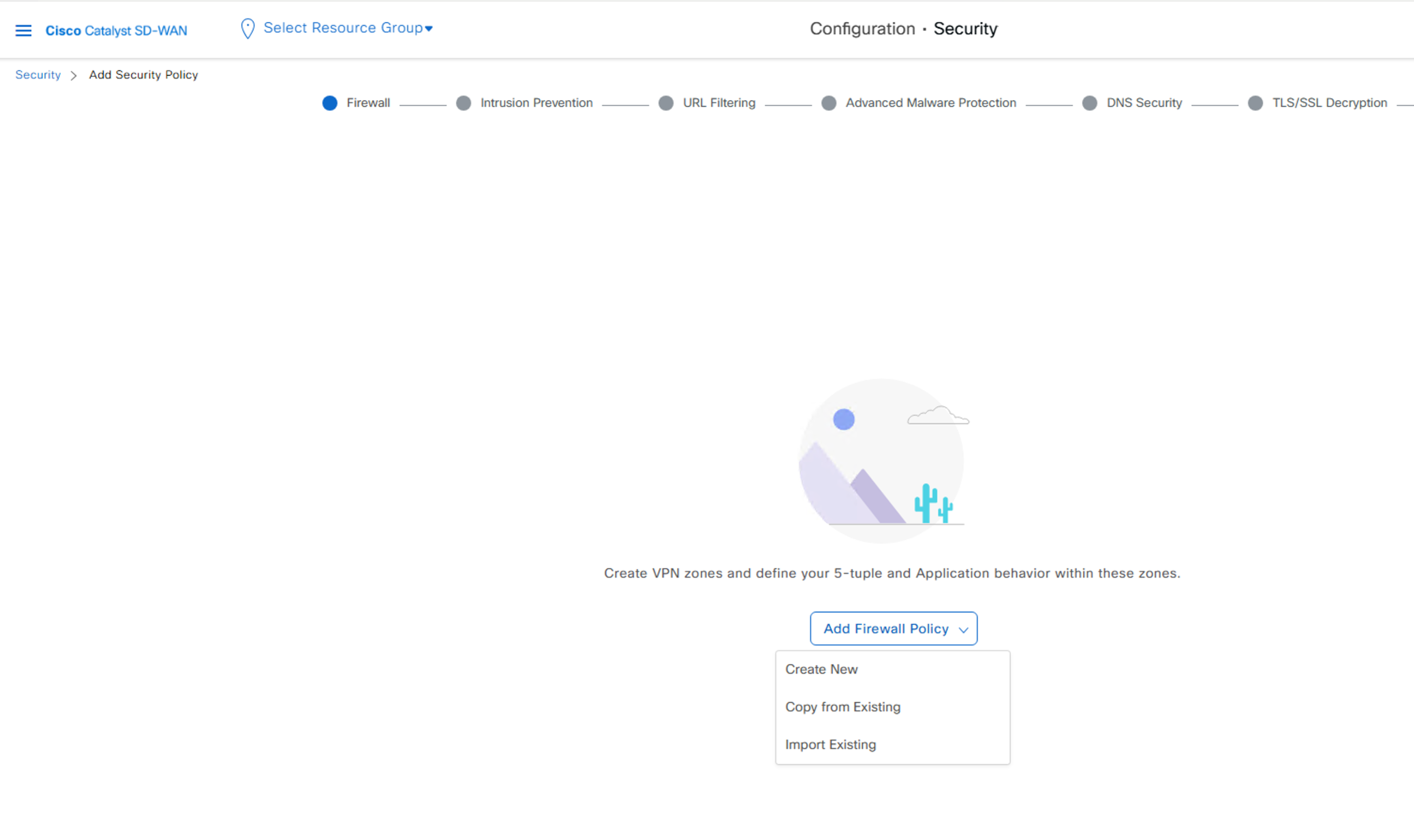
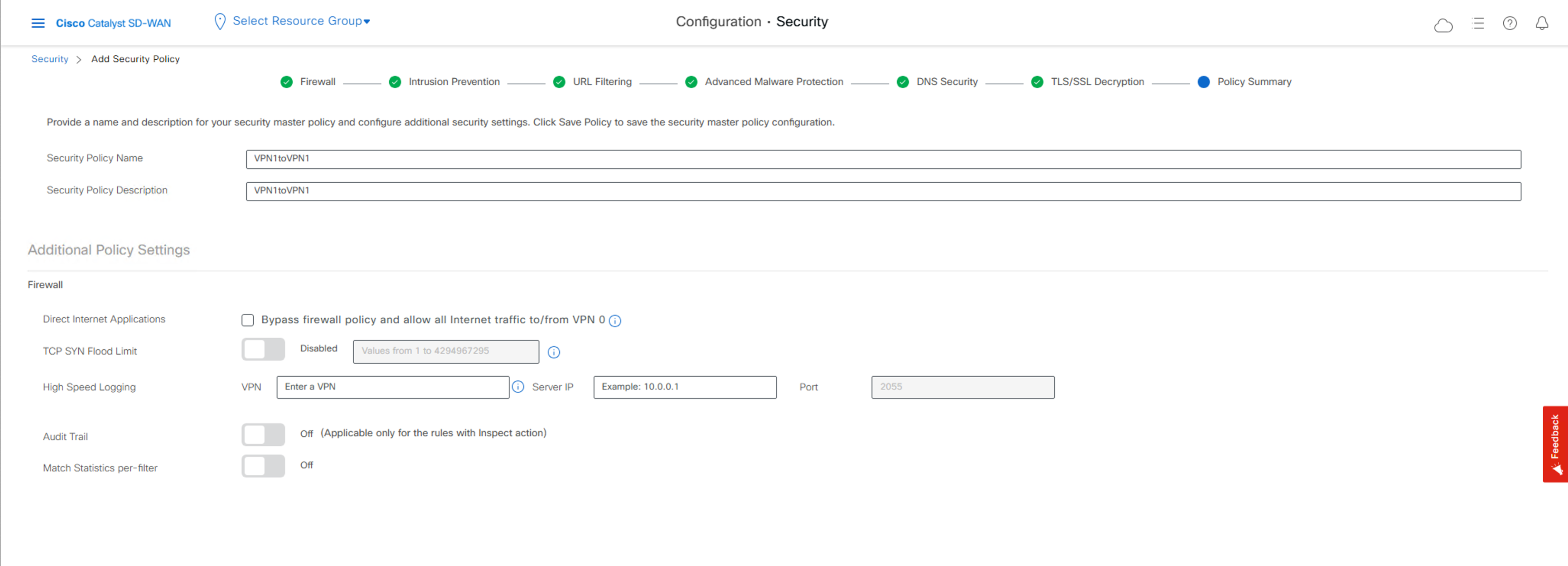
vManage:Configuration -> Security -> Add Security Policy -> Custom -> Add Firewall Policy (Create New)
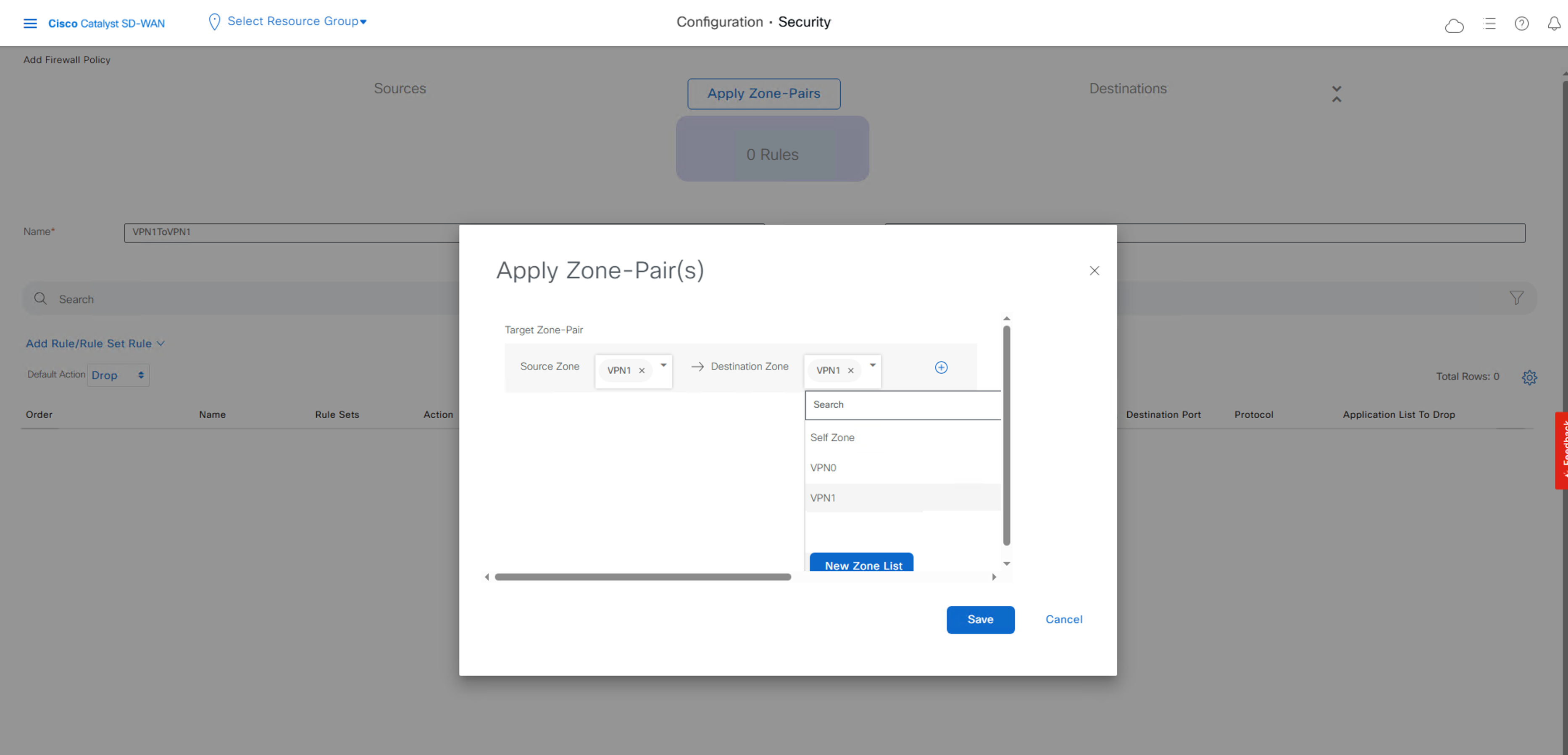
创建 Zone-Pairs, VPN1 to VPN1
Add Rule / Rule Set Rule
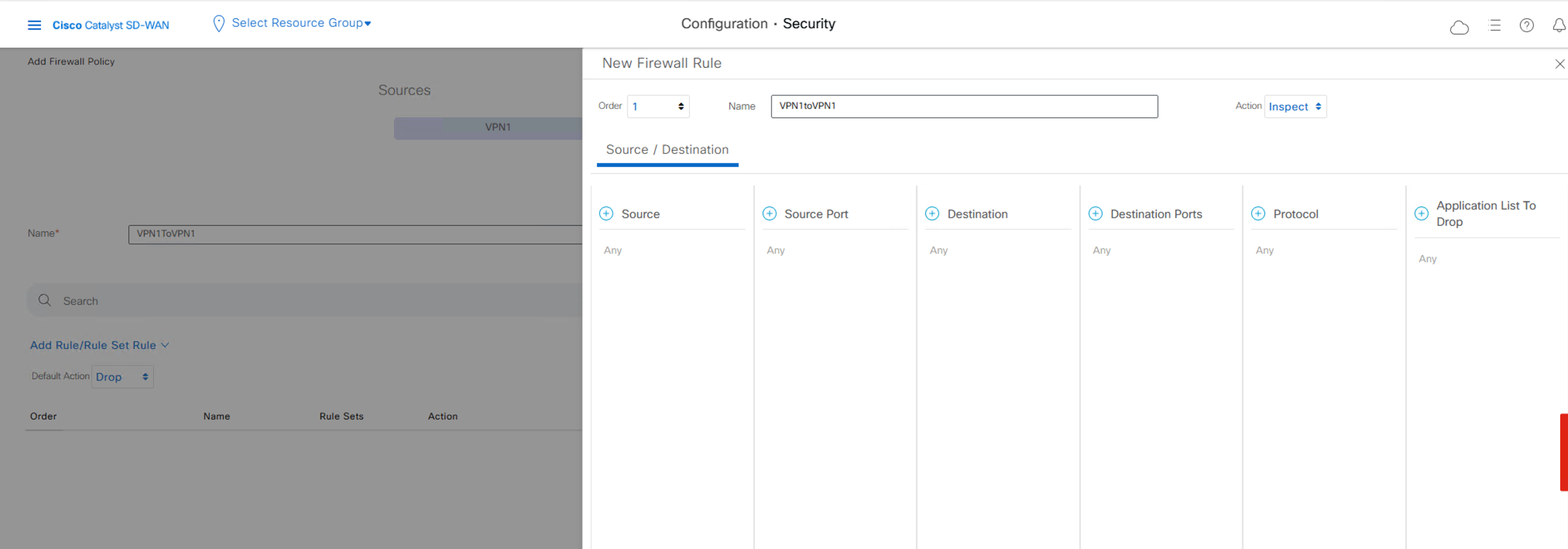
其他的保持默认:
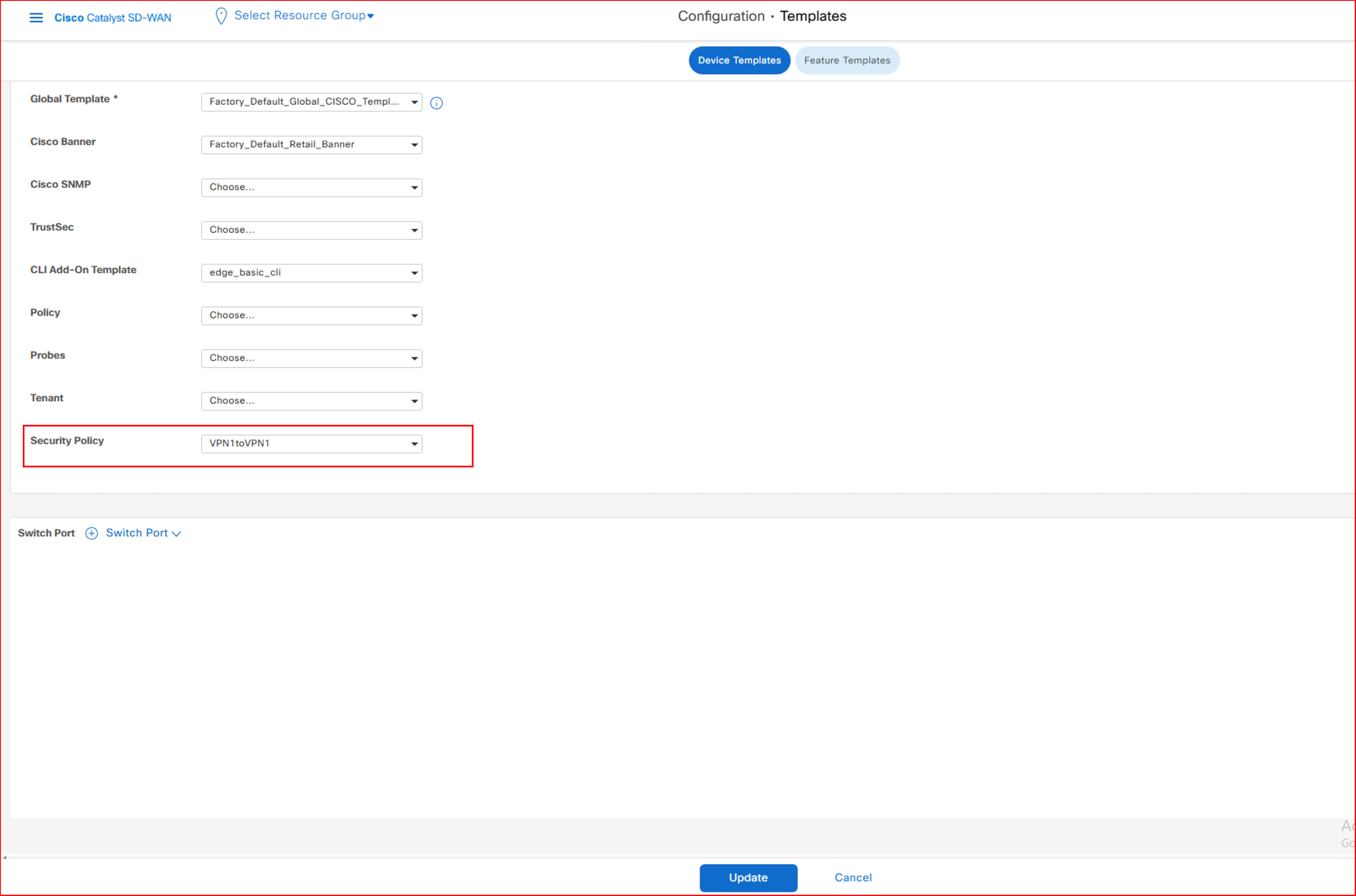
vManage:Configuration -> Templates -> Device Template -> Modify Security Policy
CLI 模板 #
===== Zones =====
zone security VPN1
vpn 1
!
===== ACL / Class =====
object-group service VPN1ToVPN1-VPN1toVPN1-svc_
ip
exit
!
ip access-list extended VPN1ToVPN1-seq-VPN1toVPN1-acl_
11 permit object-group VPN1ToVPN1-VPN1toVPN1-svc_ any any
!
class-map type inspect match-all VPN1ToVPN1-seq-1-cm_
match access-group name VPN1ToVPN1-seq-VPN1toVPN1-acl_
!
===== Policy:跨站点出站(VPN1 -> OVERLAY -> VPN1)=====
policy-map type inspect VPN1ToVPN1
class type inspect VPN1ToVPN1-seq-1-cm_
inspect
!
class class-default
drop
!
!
zone-pair security ZP_VPN1_VPN1_VPN1ToVPN1 source VPN1 destination VPN1
service-policy type inspect VPN1ToVPN1
!
验证与输出示例 #
验证 Zone 和成员以及策略绑定 #
Edge1#show zone security
zone self 65535
Description: System defined zone
zone service 65534
Description: System defined zone
Member VPN:
vpn 65528
vpn 65526
zone VPN1 2
Member VPN:
vpn 1
Edge1#show zone-pair security
Zone-pair name ZP_VPN1_VPN1_VPN1ToVPN1 3
Source-Zone VPN1 Destination-Zone VPN1
service-policy VPN1ToVPN1
Edge1#show policy-map type inspect zone-pair
Zone-pair: ZP_VPN1_VPN1_VPN1ToVPN1
Service-policy inspect : VPN1ToVPN1
Class-map: VPN1ToVPN1-seq-1-cm_ (match-all)
Match: access-group name VPN1ToVPN1-seq-VPN1toVPN1-acl_
Inspect
Packet inspection statistics [process switch:fast switch]
icmp packets: [0:906]
Session creations since subsystem startup or last reset 2
Current session counts (estab/half-open/terminating) [1:0:0]
Maxever session counts (estab/half-open/terminating) [2:0:0]
Last session created 00:00:56
Last statistic reset never
Last session creation rate 2
Last half-open session total 0
Class-map: class-default (match-any)
Match: any
Drop
0 packets, 0 bytes
检查 ZBFW 会话 #
Edge1#show policy-map type inspect zone-pair sessions
Zone-pair: ZP_VPN1_VPN1_VPN1ToVPN1
Service-policy inspect : VPN1ToVPN1
Class-map: VPN1ToVPN1-seq-1-cm_ (match-all)
Match: access-group name VPN1ToVPN1-seq-VPN1toVPN1-acl_
Inspect
Established Sessions
Session ID 0x00000004 (192.168.1.2:8)=>(192.168.2.2:8) icmp SIS_OPEN
Created 00:02:25, Last heard 00
Bytes sent (initiator:responder) [8176:8176]
Class-map: class-default (match-any)
Match: any
Drop
0 packets, 0 bytes
Edge1#show sdwan zonebfwdp sessions
SRC DST TOTAL TOTAL UTD
SESSION SRC DST SRC DST VPN VPN NAT INTERNAL INITIATOR RESPONDER APPLICATION POLICY
ID STATE SRC IP DST IP PORT PORT PROTOCOL VRF VRF ID ID ZP NAME CLASSMAP NAME FLAGS FLAGS BYTES BYTES TYPE NAME
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
4 open 192.168.1.2 192.168.2.2 8 8 PROTO_L4_ICMP 3 3 1 1 ZP_VPN1_VPN1_VPN1ToVPN1 VPN1ToVPN1-seq-1-cm_ - 306 17192 17192 -
检查 ZBFW 丢包 #
Edge1#show platform hardware qfp active statistics drop
Last clearing of QFP drops statistics : never
-------------------------------------------------------------------------
Global Drop Stats Packets Octets
-------------------------------------------------------------------------
FirewallInvalidZone 5 490
FirewallL4 4 464
Ipv4NoAdj 1 56
Ipv4RoutingErr 205 20090
Ipv6NoRoute 4 224
Nat64v6tov4 6 480
SdwanImplicitAclDrop 42353 2457839
UnconfiguredIpv6Fia 57 4086
Edge1#show platform hardware qfp active feature firewall drop all <<< 详细丢包内容
-------------------------------------------------------------------------------
Drop Reason Packets
-------------------------------------------------------------------------------
Invalid L4 header 0
Invalid ACK flag 0
Invalid ACK number 0
Invalid TCP initiator 0
SYN with data 0
Invalid window scale option 0
Invalid Segment in SYNSENT 0
可以用 packet trace 去抓取丢包的详细内容去判断, 比如 tcp flag 位是否正确
debug platform condition interface GigabitEthernet0/0/1 ipv4 x.x.x.x/32 both
debug platform packet-trace packet 2048 fia-trace data-size 2048
debug platform packet-trace copy packet both l2 size 2048
debug platform packet-trace drop // 设定只抓去drop的包, 如果需要查看详细的数据包交互可以不配置这一条
debug platform condition start // 开始抓包
<test>
debug platform condition stop
show platform packet-trace statistics
show platform packet-trace summary
show platform packet-trace packet <Number> 查看某一个数据包的详细信息 , 看看有有没有FirewallL4 的。
show platform packet-trace packet <Number> decode
事例:
SDWAN-cEdge-site-1902#show platform packet-trace summary
Pkt Input Output State Reason
0 Gi2 Gi1 DROP 187 (FirewallPolicy)
1 Gi2 Gi1 DROP 187 (FirewallPolicy)
2 Gi2 Gi1 DROP 187 (FirewallPolicy)
3 Gi2 Gi1 DROP 187 (FirewallPolicy)
SDWAN-cEdge-site-1902#show platform packet-trace packet 0 decode
Packet: 0 CBUG ID: 0
Summary
// 如果show platform packet-trace summary 显示抓到的数据包不多的话可以直接采集show platform packet-trace packet all 显示所有数据包的信息
// 完成以上测试抓到数据包后, 可以清除上面的debug 设定和packet buffer
show platform conditions
show platform packet-trace configuration
clear platform packet-trace statistics --> 清除packet buffer
clear platform condition all --> 清除上面配置的debug condition
排障命令 #
#show clock
#show sdwan run
#show platform hardware qfp active statistics drop
#show platform hardware qfp active feature firewall drop all
#show sdwan zbfw drop-statistics
#show sdwan zbfw zonepair-statistics
等待5分钟
#show clock
#show platform hardware qfp active statistics drop
#show platform hardware qfp active feature firewall drop all
#show sdwan zbfw drop-statistics
#show sdwan zbfw zonepair-statistics
#show zone security
#show zone-pair security
#show policy-map type inspect zone-pair
#show policy-map type inspect zone-pair sessions
#show sdwan zonebfwdp sessions
比较常见的 ZBFW(inspect)出现的 FirewallL4 丢包是由于非对称路由导致的, TCP 三次握手的数据包不全经过一台设备导致 ZBFW session 无法顺利建立, 后续的数据包会被丢弃(Invalid Segment in SYNSENT)。
这种问题需要解决非对称路由的问题, 保证所有流量都经过本台设备。 如果无法解决非对称路由, 那只能改成 pass 而不是 inspect(无状态放行,允许返回包绕路,但失去会话保护)
policy-map type inspect VPN1ToVPN1
class type inspect VPN1ToVPN1-seq-1-cm_
inspect <<<< 修改成pass
!
class class-default
drop
!
!
- 不同站点之间的流量 inspect 如果要匹配 vpn 的话,虽然对于本设备而言流量是走 vpn x to vpn 0 overlay, 但实际上流量匹配的是 vpn x to vpn x
- 或者使用 Interface Based Zones,Configure Interface Based Zones and Default Zone Using the CLI