一个简单的从 global rib 往 vrf 内 leak 路由的配置案例.
RP/0/0/CPU0:PE4#show run vrf A
Sun Mar 28 16:35:18.881 UTC
vrf A
address-family ipv4 unicast
import from default-vrf route-policy test advertise-as-vpn <<<<<<<
import route-target
1:1
!
export route-target
1:1
!
!
!
RP/0/0/CPU0:PE4#
RP/0/0/CPU0:PE4#
RP/0/0/CPU0:PE4#show run route-policy test
Sun Mar 28 16:35:28.070 UTC
route-policy test
if destination in test then
pass
else
drop
endif
end-policy
!
RP/0/0/CPU0:PE4#
RP/0/0/CPU0:PE4#show run prefix-set test
Sun Mar 28 16:35:34.210 UTC
prefix-set test
11.11.11.11/32
end-set
!
RP/0/0/CPU0:PE4#
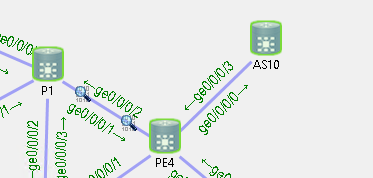
如图 PE4 从 CE 测收到 11.11.11.11/32 的路由放入 default vrf 下, 然后 leak 到 vrf A 中, 若需要将此 leak 的路由通过 vpnv4 邻居通告给其他路由器如 P1,需要在 import vrf 的时候加“advertise-as-vpn” 关键字.
RP/0/0/CPU0:PE4#show bgp ipv4 unicast 11.11.11.11/32
Sun Mar 28 16:41:10.876 UTC
BGP routing table entry for 11.11.11.11/32
Versions:
Process bRIB/RIB SendTblVer
Speaker 9 9
Last Modified: Mar 26 10:52:55.657 for 2d05h
Paths: (1 available, best #1)
Not advertised to any peer
Path #1: Received by speaker 0
Not advertised to any peer
10
10.1.12.2 from 10.1.12.2 (192.168.0.10)
Origin IGP, metric 0, localpref 100, valid, external, best, group-best, import-candidate
Received Path ID 0, Local Path ID 1, version 9
Origin-AS validity: (disabled)
RP/0/0/CPU0:PE4#
RP/0/0/CPU0:PE4#show bgp vrf A ipv4 unicast 11.11.11.11/32
Sun Mar 28 16:42:44.220 UTC
BGP routing table entry for 11.11.11.11/32, Route Distinguisher: 1:2
Versions:
Process bRIB/RIB SendTblVer
Speaker 52 52
Local Label: 24012
Last Modified: Mar 26 11:06:14.657 for 2d05h
Paths: (1 available, best #1)
Not advertised to any peer
Path #1: Received by speaker 0
Not advertised to any peer
10
10.1.12.2 from 10.1.12.2 (192.168.0.10)
Origin IGP, metric 0, localpref 100, valid, external, best, group-best, import-candidate, imported
Received Path ID 0, Local Path ID 1, version 52
Extended community: RT:1:1
Origin-AS validity: (disabled)
Source AFI: IPv4 Unicast, Source VRF: default, Source Route Distinguisher: 0:0:0
RP/0/0/CPU0:PE4#
Other Way import prefix #
Community #
route-policy dyna-route-leak-comm-9-x
if community matches-every (65008:9) then
pass
endif
end-policy
vrf vrf2
address-family ipv4 unicast
import from default-vrf route-policy dyna-route-leak-comm-9-x
import route-target
1:2
As-path/prefix #
route-policy dyna-route-leak-aspath-prefix-10-x
if as-path originates-from '65008' and destination in (10.0.0.0/24) then
pass
endif
end-policy
!
vrf vrf3
address-family ipv4 unicast
import from default-vrf route-policy dyna-route-leak-aspath-prefix-10-x
import route-target
1:3
Refer:
https://learningnetwork.cisco.com/s/question/0D53i00000KstGr/ios-xr-leaking-the-routes-between-vrf-and-global-rib
https://community.cisco.com/t5/service-providers-documents/cisco-bgp-dynamic-route-leaking-feature-interaction-with-juniper/ta-p/3139676